| 1. | ||
| 2. | ||
| 2.1. | ||
| 2.2. | ||
| 2.3. | ||
| 2.4. | ||
| 3. | ||
| 4. | ||
Importance of Network Security for Business Organization
Razauddin Mohammed Salim
Vishweshwarya Institute of Engineering and Technology, UPTU, Ghaziabad, U.P. India
Email address
Citation
Razauddin Mohammed Salim. Importance of Network Security for Business Organization. American Journal of Computer Science and Information Engineering. Vol. 3, No. 6, 2016, pp. 45-49.
Abstract
In this paper, an attempt has been made to review the various Network Security and Cryptographic concepts. This paper discusses the state of the art for a broad range of cryptographic algorithms that are used in networking applications This paper also highlights the terms of computer security and network security. I would like to study the issues like password security, network sniffing, intrusion detection, firewalls and network structure in detail. As the risks are many in a business organization, there should be a complete system dedicated to securing the networks. We will also discuss malicious users that why they do not possess a high level of programming skills and instead make use of tools available on the Internet.
Keywords
Network Security, Password, Network Sniffing Firewalls, Network Structure
1. Introduction
Any organization should monitor its system for potential unauthorized access and other kind of attacks. In order to safeguard sensitive information, it is important to perform routine checks and create a reliable and safe network. Every year, many organizations, corporations and governments dedicate a substantial chunk of their investment on their computer and network security. It is crucial to establish a safe and secure network for the following reasons:
1. To Protect Company’s Assets
2. To Comply with Regulatory Requirements and Ethical Responsibilities
3. For Competitive Advantage
Technology has progressed so much that it would be no surprise if your computer is hacked and you are completely unaware of the reasons for it. On a personal level, the network security includes only the downloading and installation of anti-virus software and firewall settings. However, when the same problem arises in a business organization, then the solution cannot be as simple as in the personal computer networks. As the risks are many in a business organization, there should be a complete system dedicated to securing the networks.
When the term computer security is used, it specifically refers to the security of one computer, although the overall security of each individual computer is required for network security. When the term network security is used, it refers to the security of the network in general. This includes such issues as password security, network sniffing, intrusion detection, firewalls, network structure and so forth.
Top security issues that will destroy computer
1. Targeted Attacks
2. More Hactivism
3. Increase in Malware
4. Privacy Rights Eroding
5. Cyber Extortion
6. Android, Even Worse
7. Un-Patched Exploits In Java
2. Why Is Network Security Important?
Network Security helps to secure the computer network infrastructures. It plays an important role in computer networking field. Nowadays piracy has become a major concern for any organization. Hackers are very active and their tools become sharper. This requires security policy to implement for internal and external threats of network security. It is an consequential part of system administration. The aim of this paper is to focus on purpose of network security and types of threats that it faces during the implementation of a security strategy.
2.1. Importance of Network Security?
While discussing importance of network security there are few questions that need to be discussed-:
1. What is the most private, embarrassing or valuable piece of information you’ve ever stored on a computer
2. How much you rely on computer systems to be available
3. When you need them
4. The degree to which you question whether a piece of email really came from the person listed in the From field
5. How convenient it is to be able to access private information online (e.g. buy without entering all data, look up your transcript without requesting a copy)
It is our jobs as professional computer scientists to evaluate -:
1. The systems we use
2. To understand their weaknesses
3. To educate ourselves and others to be wise
4. Network consumers
5. To design networked systems that are secure
Network Security can also be defined as the protection of a computer network and it services from unauthorized modification, destruction, or disclosure. Network security is becoming of great importance because of intellectual property that can be easily acquired through the internet; so to understand the importance and even the future of networking; one must review the history and emergence of network security.
2.2. Using Cryptography
Uses of Cryptography –There are 4 main uses of cryptography
1. Secrecy/Confidentiality
2. Authentication
3. Integrity.
4. Nonrepudiation
Example 1:
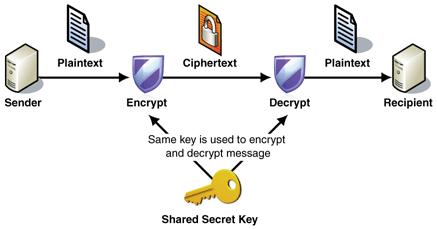
Example 2:
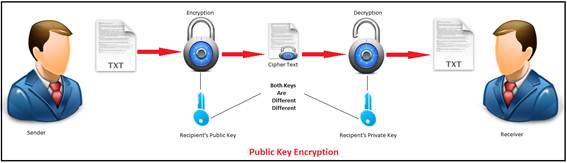
Example 3: Secret key cryptography
With secret key cryptography, a single key is used for both encryption and decryption. As shown in Figure 1, the sender A uses the key K (or some set of rules) to encrypt the plaintext message M and sends the ciphertext C to the receiver. The receiver applies the same key K (or ruleset) to decrypt the cipher text C and recover the plaintext message M. Because a single key is used for both functions, secret key cryptography is also called symmetric encryption.
With this form of cryptography, it is obvious that the key must be known to both the sender and the receiver; that, in fact, is the secret. The biggest difficulty with this approach, of course, is the distribution of the key.
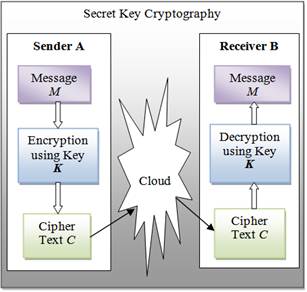
Figure 1. Shows secret key Cryptography.
2.3. What Are Some Popular Networks?
We are using a number of networks and networks protocols which were defined from more than two decades. We are going to look some of these networks here which are based on size:
2.3.1. Personal Area Network (PAN)
It is an organized computer network around a person in a room, an office or in a single building. When it is used by more than a single individual in same premises, the networks also referred as Home Area Network (HAN). It includes computers, telephones, video game consoles, personal entertainment devices and other peripheral devices.
PAN or HAN allow us to:
1) To print a document while sitting on a couch when the printer is upstairs.
2) To upload pictures and videos to personal desktop computer.
3) Online streaming to watch a movie on a TV.
Example shown in figure 2.
Figure 2. Shows Personal Area Network (PAN).
2.3.2. Local Area Network (LAN)
It is a computer network that is used in an individual office building, residence, school, labs and university campus. The computers are geographically very close together.
It has only two computers in a smallest LAN or can accommodate thousands of computers in larger LAN. It can be wired or wireless connection but wired connection increases its speed and security. If a LAN is completely wireless is known as WLAN. In LAN, all computers and other devices are connected through a cable using different types of topologies like Bus, Star, Ring and Tree etc. LAN follow client–server methodology, in which one computer serves as a sever and remaining computers as clients. All applications and software are stored on server and it can be used by other computers (clients). See the figure 3 below for LAN.
Figure 3. Illustrate Local Area Network (LAN).
2.3.3. Metropolitan Area Network (MAN)
Metropolitan Area Networks cover larger area than a LAN. It is designed for a town or a city but geographically it is smaller than Wide Area Network (WAN). It interconnects several LAN to make a bigger network. MAN is an intermediate of LAN and WAN that covers an area the size of a city. It is not owned by a single user but owned a single network provider who sells services to the user. It allows users to share regional resources and act as a high speed network.
See MAN example in figure 4.
Figure 4. Shows Metropolitan Area Network (MAN).
2.3.4. Wide Area Network (WAN)
Wide Area Networks or WAN, generally covers a larger area geographically. It connects different local area networks (LAN) and metropolitan area networks (MAN). It spans across cities, states or countries. WAN uses communication circuits to do this. WAN design and performance requires lease communications circuit from telephone companies and other communication carrier. WAN covers a wide area as compared to LAN. Therefore it has large volume of traffic. This traffic needs controlling and excessive delay. Hence the topologies are more complex than LAN. The largest WAN example is internet.
Figure 5 shows the example of WAN.
Figure 5. Illustrate Wide Area Network (WAN) or Internet.
2.4. Analysis on Various Security Concepts of Network and System Devices
Files and resources can be shared easily with the help of Network devices. These are the components that connect computers and other electronic devices. Here we define some of the commonly used network devices:
1. Routers: - Router is a device that connect different networks and used to send data packets between computer networks. It is a hardware that is designed to receive, analyze and move incoming packets to another network. It is an intelligent device which is slower than a bridge. It creates and maintains a table for a data packet from available routes with their conditions. Then, it uses this information with distance and cost algorithm to determine the best route for the same data packet. Therefore it is necessary to understand the routing as well as behavior of network layer protocol.
2. Switches: - Switch is a device that creates a network. It is a device of computer networking that connects other devices on a computer network. It is a controller that enables networked devices to communicate efficiently. It uses packet switching in which it receives and process data, then forwards it to destined device.
3. Firewall: - Firewall is a hardware or software or combination of both that act as a barrier between trusted and untrusted networks over a predetermined security rules. It is a system that is designed to monitor and control incoming and outgoing traffic of network system. It protects both a home network as well as corporate networks.
4. Wireless and Mobile Communications: - Wireless communication is the transfer of information or power between two or more points that are not connected by an electrical conductor. The most common wireless technologies use radio.
3. Discussion
Following points will describe how and what exactly is network security contains. These points make us clear that in today’s world network security plays a very important role.
1. Network Security helps in protecting personal data of clients existing on network.
2. Network Security facilitates protection of information that is shared between computers on the network.
3. Hacking attempts or virus / spyware attacks from the internet will not be able to harm physical computers. External possible attacks are prevented.
4. Network Security provides different levels of access. If there are various computers attached to a network, there may be some computers that may have greater access to information than others.
5. Private networks can be provided protection from external attacks by closing them off from internet. Network Security makes them safe from virus attacks, etc.
Network security is necessary to protect our data and business. Apart from it network monitoring and security helps in improve performance of a business. If we don't have strong, healthy and secure network, then all secrete data can be leaked and as resultant it can make a very big loss.
4. Conclusion
With the advent of the World Wide Web and the emergence of e-commerce applications and social networks, organizations across the world generate a large amount of data daily. So data security is the utmost critical issue in ensuring safe transmission of information through the internet. Also network security issues are now becoming important as society is moving towards digital information age. As more and more users connect to the internet it attracts a lot of cyber-criminals. It comprises authorization of access to information in a network, controlled by the network administrator. The task of network security not only requires ensuring the security of end systems but of the entire network.
The paper presented various schemes which are used in cryptography for Network security purpose. Encrypt message with strongly secure key which is known only by sending and recipient end, is a significant aspect to acquire robust security in cloud. The secure exchange of key between sender and receiver is an important task. The key management helps to maintain confidentiality of secret information from unauthorized users. It can also check the integrity of the exchanged message to verify the authenticity. Network security covers the use of cryptographic algorithms in network protocols and network applications. This paper briefly introduces the concept of computer security, focuses on the threats of computer network security
In the future, work can be done on key distribution and management as well as optimal cryptography algorithm for data security over clouds
References