Fingerprint Recognition System Within a High Public Insecurity Context
Kanaa Thomas F. N.1, 2, Ele Pierre3, Tchiotsop Daniel4, Tonye Emmanuel5
1Higher Technical Teacher Training College, University of Bamenda, Bambili, Cameroon
2Laboratory of Electronics, Electrotechnics, Automation and Telecommunications, University of Douala, Douala, Cameroon
3University Institute of Technology, Laboratory of Electronics, Electrotechnics, Automation and Telecommunications, University of Douala, Douala, Cameroon
4Fotso Victor University Institute of Technology, Laboratory of Automation and Applied Computer Science, University of Dschang, Bandjoun, Cameroon
5National Advanced School of Engineering, Laboratory of Electronics and Signal Processing, University of Yaounde I, Yaounde, Cameroon
Email address

(Kanaa T. F. N.)

(Ele P.)

(Tchiotsop D.)

(Tonye E.)
Citation
Kanaa Thomas F. N., Ele Pierre, Tchiotsop Daniel, Tonye Emmanuel. Fingerprint Recognition System Within a High Public Insecurity Context. International Journal of Electrical and Electronic Science. Vol. 3, No. 5, 2016, pp. 26-35.
Abstract
This paper is presenting a new and robust fingerprint identification/verification method liable to minimize any risk of human loss and to preserve peace and freedom when fighting against terrorism in a context of high public insecurity. For that matter, a database of 200 fingerprint images from a Boko Haram risk region of Cameroon has been put in place on which a noteworthy method from the literature and the author’s algorithm were tested. For this last algorithm, the enhanced image is computed by convolution of the Gabor filter attached to the ridge orientation and the ridge frequency, with the normalized fingerprint image from the minutiae rough segmentation by global thresholding on the variance. The minutiae are extracted gradually with the local Sauvola’s thresholding, the parallel thinning algorithm of the ridges and the false minutiae removal technique based on its branch. A minutia alignment and an elastic matching algorithm based on the optimization of the bounding box tolerance parameters are then combined to provide the matching score of the input fingerprint. With an accuracy of 99.27% at the equal error rate position, an improvement of 33.91% is observed as gap between the classical and the new approaches. The improved technique faithfully recognizes the fingerprints of the same individual and strongly rejects two different individuals’ fingerprints. An innovative development is therefore ready for detecting genuine and intruders in control systems to better solve the identification and verification problems in high public insecurity environments where a high performance is henceforth imposed as critical and strategic requirement in the whole world.
Keywords
Biometrics, Fingerprint, Segmentation, Minutiae Matching, Gabor Filtering, Sauvola’s Thresholding
1. Introduction
The relationship between biometrics and anthropology is far more significant in the biometric systems performances. In their book, Pato et al. [1] engage a presentation opening the links between the cultural, social and legal considerations in biometrics verification. There are relevant aspects such as interaction of biometric systems and individuals, universality and potential disenfranchisement, individuality and geographical identity, to gather in the evaluation and harmonization of biometric systems from their performance. In a similar intention, Maguire [2] outlined the need to know the individuals evaluated, because of their cultural and morphological traits of development. The history of Biometrics has evolved in years and the evaluation of the biometric systems should be performed on a known population. Mordini et al [3] went further in revealing biometrics as tools of natural group identification.
As far as public insecurity is concerned, biometrics is the most used tool. Since intruders’ nature or identity is never known or predictable, the whole world becomes concerned. The occurrence of crisis and terrorism globally, is an alarm for security improvement. The Islamic State (ISIL), the Tehrik-i-Taliban Pakistan (TTP), the Lords Resistance Army, the Insurgents, the extremists, the militias, the rebel groups … just to name a few, have certainly established a general climate of fear in the whole world and above all expectations, an increase of 80% representing 14,574 deaths between 2013 and 2014 [4]. Boko Haram in the recent past, added its name on that incomplete list.
Using Biometrics in Africa for a regional or global purpose is not an operation of spontaneous generation, Delgado [5] highlighted in his report that Liberia has been the pioneer in using biometrics on registering refugees because of their potential recruitment by rebel groups. The standard registration and identification of population through birth certificate is no more secure; it has proved its limits in terms of security and exhaustive identification and verification [6, 7]. In these outdated identification documents, anybody can be anyone and all the identification and verification systems are evolving to be more dynamic and performed in real time. Even if the public and individual privacies condemned legally certain practices in global controls, developed countries are nonetheless voting laws for deep individual and group controls [8].
Biometric systems are the developments and the constant implementations in the history of traditional and modern worlds, because of their substance and impact. The more complex the function to appreciate is, the more performant must be the system. The system performance doesn’t therefore depend only on the accuracy in the recognition, but also in the answering-speed [9]. Traditionally, two major types of automatic personal identification approaches have been widely used: knowledge-based and token-based [10]. Tokens such as credit card, keys and driver licenses may be lost, stolen, forgotten or misplaced. PIN and password may be forgotten or guessed by the impostors. This problem has led to the use of fingerprint recognition systems in area or domains where high level of security is needed. Biometric techniques based on fingerprint recognition have been used for personal identification during many centuries and the matching accuracy has been shown to be very high [11]. An explanation of a wide use of the fingerprint compared to the facial recognition is also based on the natural aging phenomenon and the potential accidents that may occur on the face [5, 12]. Authentication methods, promoted by Biometrics, have been tested in practical system [13-16]. Drahansky [17], as many other authors [11, 18, 19], defines the three main steps in the biometric developments as enrollment, identification and verification.
On human fingerprints, basic ridges patterns known as loop, arch and whorl, contain crossover, core, bifurcation, ridge ending, island, delta and pore, but two types of singular points can be defined in terms of the ridge-valley structures: the core and the delta [20, 21, 22]. Each fingerprint contains maximal 2 cores and 2 deltas [20, 21]. The National Institute of Standards and Technology [19] proposed a minutiae-based fingerprint representation. It includes minutiae location and orientation [11, 19]. So, minutiae points in a fingerprint are represented according to three parameters the x-coordinate, the y-coordinate and the ridge orientation. And a minutiae-based generic biometric verification system makes two types of errors false match rate (FMR) and false non-match rate (FNMR). The similarity score, the threshold, the genuine score and the impostor score are some important parameters to take into consideration while designing a fingerprint recognition system [11, 23, 24].
The evolution of technology completely transformed the extraction of fingerprint patterns which, traditionally, was performed through the inked impression of the fingertip on paper called by then offline acquisition. Thus, the online technique rather uses a mean of varied sensors known as fingerprint scanners [11].
A number of methods have been developed in recent years for automatic fingerprint recognition. They are usually developed either in the improvement of the image enhancement, the minutiae detection and extraction or finally in the matching techniques classified in three big families: Minutiae-based matching, Correlation-based matching and Ridge feature-based matching [22, 25, 26].
For the image enhancement, Alessandro et al. [27] proposed a new approach for bridge cleaning based on ridge positions. They used two novel criteria and related algorithms for validating the endpoints and bifurcations. In a different push but with the same aim, Shlomo et al. [28] also proposed two different methods for fingerprint ridge image enhancement: image binarization based method and direct gray-scale images. The first one is carried using histogram equalization, Wiener filtering, while the second method uses a unique anisotropic filter for direct gray-scale enhancement. In the same line, a true success rate (TSR) of 85% in the matching exercise with the FVC 2004, Jossy et al. [29] proposed an algorithm based on the Dual Tree Complex Wavelet Transform Domain (DTCWT). The features are generated from the coefficient of the DTCWT algorithm and the system performance is estimated through the same DTCWT levels.
Using the FVC 2004 database, Liu Wei-Chao et al [30] presented a recognition algorithm for occluded fingerprint which is comparing images and templates through the multi association features matching. The Gabor filter for the image enhancement, the binarization and thinning helped to complete the preprocessing of images. The features extraction is done in image subsets and then compared to the template. An accuracy of 94.72% is recorded for non-occluded fingerprint image and another one of 93.76% for occluded images. The comparison between their model RA-MAMF through the multi-subset match strategy and three other models namely traditional algorithm, SM algorithm and SCC algorithm is performed to appreciate the strength of their approach.
The minutiae detection and/or extraction brought together so many ideas. And so, Ravi et al. [31] after a substantial literature review, used the block filter algorithm for fingerprint thinning which scans the image at the boundary to preserves the quality of the image and extract the minutiae from the thinned image. From a different methodology, Lokhande et al. [32] made use of the histogram equalization to enhance the fingerprint quality. After extracting the features in the thinned image, back-propagation neural network and cellular neural network are used for the recognition process.
In the improvement of the matching methods, Prajakta et al. [33] proposed a filter-based algorithm which uses a bank of Gabor filters to capture both local and global details in a fingerprint as a compact fixed length finger code. With the Artificial Neural Networks Hamsa (2012) [34] came out with a fingerprint recognition system to provide an efficient matching algorithm for fingerprint authentication. Ravi et al. [31] cited before, reinforced their minutiae extraction with the minutiae matching, comparing the point of the test fingerprint image with those of the template through the crossing number and the minutiae identification. The matching methods proposed by Bhawna Negi et al, [25] presented a projection of Fingerprint recognition through Minutia Score Matching method. After data extraction and storing in matrix format, template and input minutiae are taken as references. Then, a comparison between the fingerprint test and the references is performed.
With the upgrading process of all the main steps in fingerprint recognition, Yuliang He et al., [35] developed an algorithm based on orientation fields of enhanced fingerprint images. They implemented an improved Jain’s minutiae matching algorithm based on the change in the alignment method, the introduction of ridge information in the matching process and the utilization of variable bounding box in the matching of fingerprints. A noteworthy method had been implemented by Sangram et al [22] dealing with the minutiae matching in fingerprint recognition system with filtering in a frequency domain. They deployed their method on the identification and side by side comparison of ridge ending and bifurcation. With the ridge thinning, minutiae marking, false minutiae removal and minutiae representation, they achieved at a rate of almost 70%, the verification of the algorithm. The global principle is redrafted at the beginning of the process and completed by a graph matching approach to fingerprint verification [36]. The results are fully illustrated on two image samples, unfortunately without any evaluation of performances.
Jain et al. [9] developed a faster and more accurate algorithm based on the minutiae direction similitude. A virtually exhaustive overview in biometrics helped them to point out the recent developments and the challenges. The minutiae extraction deployed on orientation field estimation through the definition of the certainty level in the region of interest on the segmented image; the ridge detection is performed with the masks convolution for the accentuation of the local ridge and finally the minutiae detection is implemented through the thinning. The minutiae matching is then achieved with the alignment of point and their matching with the bounding box and its adjustment. The said methodology helped in improving the system’s response time. With an improvement of the previous, Jain et al [37] proposed a hybrid matching method that uses minutiae information and texture for matching the fingerprints. Using the algorithm of Jain [38], they performed image alignment and tessellation in cells. A bank of 8 Gabor filters was applied on cells, the feature values obtained helped to mark the matching distance. The level of matching was classified through the combination of the matching score and the minutiae-based method.
In 2012, a novel algorithm from Noor et al. [39] has been proposed. It is based on a template structure where geometrical features from the minutiae interconnection are held out to be invariant to global translation and rotation. It achieved an error equal rate at 96.5% in accuracy with significant reduction of the running time.
For comparing, classifying and improving fingerprint feature extraction using rank-level fusion, Rajanna et al. [40] clustered in the exercise two remarkable approaches based on orientation maps (OMs) and Gabor filters with two new methods based on ‘‘Minutiae Maps’’ and ‘‘Orientation Collinearity’’, all of them applied on the NIST-4 database. Using a k-NN classifier, the best accuracy of 97.76% is obtained with the Orientation Collinearity associated with Orientation Maps (CO + OM) to the disadvantage of Orientation Maps (OM), Minutiae Maps coupled with Orientation Maps (MM + OM), Gabor features, Orientation Collinearity (OC) and Minutiae Maps (MM).
Aiming at identifying fingerprints from crime scenes, a latent matching method using a descriptor-based Hough Transform for fingerprint alignment is performed in [41]. The matched pair are identified from the Euclidian distance and the direction difference, the minutiae similarity is then used to estimate the impact of each pair to provide the matching score. From the tests done on NIST SD27 database, the proposed matcher performed better than the commercial VeriFinger.
In order to classify fingerprint in classes using the random forest of oblique decision trees (RFODT), developed in his previous article, Thanh-Nghi Do et al [42] extracted local descriptors through the Hessian-affine SIFT detector elaborated by Mikolajczyk in 2004. Using seven databases, they implemented a powerful hybrid method including a series of binary SVMs to breakdown the multi-class difficulty, the Hierarchical approach and the oblique tree construction for the management of data. The results obtained set the pace with an accuracy of 95.89% over six noteworthy methods from the literature among which the Algorithm Library for Support Vector Machines (LibSVM) with One-versus-One for multi-class, AdaBoost-C4.5, Random Forests –CART, program for machine learning C4.5 and the discriminatory analysis 1-NN.
And recently, the convolutional neural networks (CNNs) for fingerprint liveness detection are performed to compare four different models [43]. Among them, the best provided an overall accuracy of 97.1% which reported an improvement compared to the best previous works.
Finally, so many interesting and performant methods have been deployed through years but a lot is still to be done in terms of developing techniques for solving regional or local crisis. The primary focus of work is to come out with a biometric system relying on fingerprints to perform recognition of people in a world regularly disturbed by terrorism and any other kind of monitored social crisis. The socio-political and strategical impacts of this disturbance have significant adverse human effect so that it urgent to prevent false identification (acceptance or rejection). Avoiding to target the genuine and to release the intruder with biometric systems within high insecurity context, compels us to implement algorithms with flawless results. In that target and taking into consideration a local database for the said contextual purposes related to insecurity and geostrategic impacts, the author’s aim is to develop a forceful system with very high accuracy and capacity in order to substantially improve fingerprint recognition.
Following therefore the summary of the current techniques for fingerprint recognition, the methodology of work presented in section 2 is dealing with the representative method of the literature and our proposed and innovative approach. The simulation results are then illustrated and commented in the third section tailed with the conclusion in section 4.
2. Methodology of Work
The work is made up of three main parts, the fingerprint image acquisition, the implementation of a conventional method, and the deployment of a new approach with a view to improve fingerprint recognition.
2.1.Fingerprint Image Acquisition
The fingerprint images have been acquired using an optical scanner DERMALOG F1, serial number F10011288, and a computer ACER BRAND of 4 Go of RAM, processor 2.20x2.20 GHz.
In a Boko Haram risk area of Cameroon, a population randomly sampled of twenty young individuals aged between 25 to 35 years old is adopted. The right thumb of each one of them is scanned ten times at different positions to constitute the database of our system.
2.2. Conventional Method
The minutiae based fingerprint recognition method used by Sangram et al. [22], is first performed. This literature method is divided into four main steps: fingerprint image preprocessing (enhancement and segmentation), minutiae extraction (thinning and marking), image post-processing (false minutiae removal), and munitiae alignment and matching. For image enhancement, histogram equalization has been applied to the original image followed by the Fast Fourier Transform (FFT) equation. The enhanced image is divided into blocks of size 32x32 and a local thresholding algorithm based on the mean is used. The segmentation is done first by computing the local ridge orientation followed by morphological operations to extract, thin and mark the minutiae by using a 3x3 structuring element. Concerning the post-processing step, an algorithm of false minutiae removal is applied. For the matching stage, we used a minutia alignment algorithm and an elastic matching algorithm described in §2.3.3, with a bounding box of size corresponding to the usual tolerance parameters 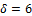 ,
, 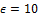 and
and 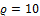 .
.
2.3. Improved Method
This approach is deployed into 3 steps: fingerprint image enhancement, minutiae extraction and minutiae matching.
2.3.1. Fingerprint Enhancement
The fingerprint enhancement from Hong et al. [44] is performed. It starts with the global thresholding applied to the variance image obtained on 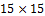 size kernels for minutiae rough segmentation. The normalized image is deduced by adjusting its values in order to get them in a desired range of intensities. The local orientation field
size kernels for minutiae rough segmentation. The normalized image is deduced by adjusting its values in order to get them in a desired range of intensities. The local orientation field 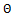 at pixel
at pixel 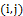 is then computed with the equation:
is then computed with the equation:
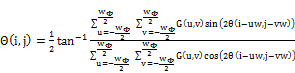 (1)
(1)
Where 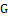 is a two dimensional Gaussian filter of size
is a two dimensional Gaussian filter of size 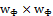 ,
, 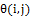 is the rough local orientation of the normalized image at the block size
is the rough local orientation of the normalized image at the block size 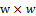 centered at pixel
centered at pixel 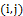 , and performed by equation 2.
, and performed by equation 2.
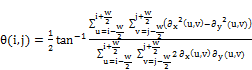 (2)
(2)
Where 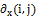 and
and 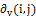 are the gradients along the two axes
are the gradients along the two axes 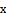 and
and 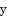 , respectively.
, respectively.
The ridge position is sinusoidal-shaped wave modeled along the normal to the local ridge orientation. Then from the normalized image and the orientation image above, the local non corrupted ridge (and valley) frequency is computed as the reciprocal of the ridge wavelength in each x-signature on the ridges coordinate system. The corrupted ridges frequency is for him interpolated from the neighboring blocks by using a discrete special Gaussian Kernel. The ridges are then characterized by the amplitude, the frequency and the variance of the corresponding sinusoidal-shape wave. An adaptive learning is performed from several fingerprint images for region classification.
Since the ridge orientation and ridge frequency information have been determined, it has been useful in constructing a bandpass filter to select true and remove false ridges. The enhanced Gabor filtering then takes over from its general even-symmetric form:
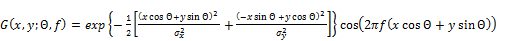 (3)
(3)
Where 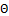 is the orientation of the Gabor filter,
is the orientation of the Gabor filter, 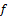 is the frequency of the cosine wave,
is the frequency of the cosine wave, 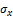 and
and 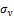 are the standard deviations of the Gaussian envelope along the x and y axes, respectively. The Gabor filter is applied to the fingerprint image by spatially convolving the image with the filter. The convolution of a pixel
are the standard deviations of the Gaussian envelope along the x and y axes, respectively. The Gabor filter is applied to the fingerprint image by spatially convolving the image with the filter. The convolution of a pixel 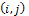 in the image requires the corresponding orientation value
in the image requires the corresponding orientation value 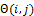 and ridge frequency value
and ridge frequency value 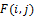 of that pixel. The Gabor filter
of that pixel. The Gabor filter 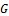 is then applied to obtain the enhanced image
is then applied to obtain the enhanced image 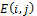 with Equation 4.
with Equation 4.
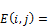
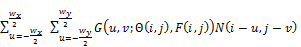 (4)
(4)
Where 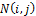 is the normalized fingerprint image,
is the normalized fingerprint image, 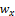 and
and 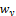 are the width and height of the Gabor filter mask, respectively.
are the width and height of the Gabor filter mask, respectively.
2.3.2. Minutiae Extraction
Knowing that the local thresholding has proved it efficiency compared to the global one, the above output fingerprint image binarization is also performed with local thresholding as on the conventional approach, with the specificity of using the followed Sauvola’s threshold [45]:
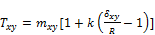 (5)
(5)
Where 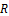 is the maximum value of the standard deviation,
is the maximum value of the standard deviation, 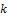 is a bias, which takes positive values in the range [0.2, 0.5],
is a bias, which takes positive values in the range [0.2, 0.5], 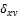 and
and 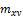 denote the local standard deviation and mean value of the set of pixels contained in a neighborhood that is centered at coordinate
denote the local standard deviation and mean value of the set of pixels contained in a neighborhood that is centered at coordinate 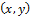 within a window of size
within a window of size 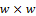 in an image.
in an image.
An efficient, fast and robust parallel thinning algorithm [46] is then applied to extract the skeleton of the ridges by eliminating the redundant pixels till they are just one pixel wide. In a 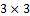 window, each pixel is connected with its eight neighbors. The technique provides with two sub iterations with behavior depending on the number of 1 patterns in the ordered set and the number of nonzero neighbors.
window, each pixel is connected with its eight neighbors. The technique provides with two sub iterations with behavior depending on the number of 1 patterns in the ordered set and the number of nonzero neighbors.
The minutiae extraction follows using the algorithm based on the specification of the branch (ridge branch, ridge end or general branch) proposed by [22] on windows of size 3x3. Seven types of false minutiae points are detected and removed according to the inter ridge distance allowed.
2.3.3. Minutiae Matching
The minutiae matching approach is effected of the same principle with the one introduced in §2.2. The aligned point pattern matching which models a main property of fingerprint impressions, that is its nonlinear deformation, is reproduced. The matching process is adaptively elastic to control the minutiae localization and orientation by using a bounding box around each template, defined by the tolerance parameters, and operating the readjustment between the template and the input minutiae [9].
In our string-matching algorithm, two matrix corresponding to the input and the template images with 4 column each, are available for comparison. The first column is the x-coordinate, the second is y-coordinate, the third is the orientation with x-axis 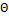 and the fourth column is the type of minutiae
and the fourth column is the type of minutiae 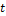 (termination or bifurcation). Let then consider these minutiae patterns as a string in the Cartesian coordinate system, with
(termination or bifurcation). Let then consider these minutiae patterns as a string in the Cartesian coordinate system, with 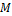 minutiae in the template and
minutiae in the template and 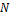 minutiae in the input image respectively so that
minutiae in the input image respectively so that 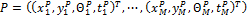 and
and 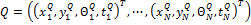 . The translation and the rotation parameters between the ridge associated with each input minutiae and the ridge associated with each template minutiae are estimated. The template and input patterns are converted into polar coordinate representation with respect to corresponding minutiae on which alignment is achieved. They are represented as two symbolic strings by concatenating each minutiae in an increasing order of radial angles as
. The translation and the rotation parameters between the ridge associated with each input minutiae and the ridge associated with each template minutiae are estimated. The template and input patterns are converted into polar coordinate representation with respect to corresponding minutiae on which alignment is achieved. They are represented as two symbolic strings by concatenating each minutiae in an increasing order of radial angles as 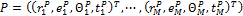 and
and 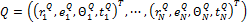 , where
, where 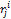 ,
, 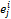 ,
, 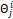 and
and 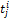 represent the
represent the 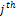 radial, radial angle, orientation and type of the minutiae with respect to the
radial, radial angle, orientation and type of the minutiae with respect to the 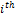 reference (input or template) minutiae.
reference (input or template) minutiae.
String matching is performed by optimization of the cost function 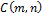 which essentially takes in consideration the penalty function
which essentially takes in consideration the penalty function 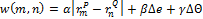 , adjusting the bounding box when an inexact match is found, especially when
, adjusting the bounding box when an inexact match is found, especially when 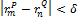 ,
, 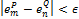 and
and 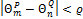 , where
, where 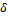 ,
, 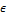 and
and 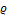 specify three bounding box tolerance parameters;
specify three bounding box tolerance parameters; 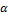 ,
, 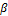 and
and 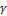 are weights attached to,
are weights attached to, 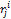 ,
, 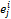 and
and 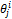 respectively,
respectively, 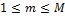 ,
, 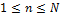 . At the end of the process, the performance of the system, especially the true success rate (TSR), depends on the size of the box defined by the tolerance parameters. The appropriate parameters
. At the end of the process, the performance of the system, especially the true success rate (TSR), depends on the size of the box defined by the tolerance parameters. The appropriate parameters 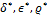 are found in order to optimize TSR at the equal error rate (EER) position (Equation 6).
are found in order to optimize TSR at the equal error rate (EER) position (Equation 6).
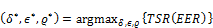 (6)
(6)
Finally, the bounding box is adjusted when 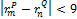 ,
, 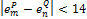 and
and 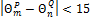 .
.
3. Data, Results and Discussion
3.1. Data
Using the optical fingerprint sensor described in section 2, a database of 200 fingerprint images acquired from 20 individuals has been created. Meaning that one person has 10 samples of his fingerprint taken from the same finger at different time. The reference code used is 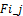 for the
for the 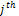 fingerprint taken from the
fingerprint taken from the 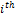 person (
person (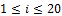 and
and 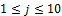 ). Two samples original images presented in figure 1, are targeted for simulation, figure 1.a displays a medium quality image and figure 1.b a very poor quality image.
). Two samples original images presented in figure 1, are targeted for simulation, figure 1.a displays a medium quality image and figure 1.b a very poor quality image.

Figure 1. Two original fingerprint images acquired with the optical fingerprint DERMALOG scanner.
3.2. Results and Interpretation
After processing of original images, the enhanced results after binarization and thinning are pertinent. The ones from the medium and the very poor quality images (figures 1.a and 1.b respectively) are shown illustration, both for the classical approach (figures 2) and the proposed method (figures 3).

Figure 2. Enhanced images obtained with the classical method on the medium quality of fig. 1.a (2.a) and the very poor quality of fig. 1.b (2.b).
In both cases the new approach performs best. There is a problem of noise removal especially in the stage of fingerprint enhancement for the classical method. This effect affects the remaining steps. The image enhancement using Fast Fourier transform does not handle the connection of broken ridges since the algorithm does not compute the local ridge orientation and frequency. The thinned fingerprint image quality is then very poor. In our proposed approach we can notice that the enhanced Gabor based enhancement technique is giving satisfactory results since it handles the problem of broken and joined ridge in the original image. The quality of the binarized and thinned fingerprint images are very good as compared to that of the classical method because of the robustness of the Sauvola’s thresholding and the fast parallel thinning algorithm used.

Figure 3. Enhanced images obtained with the new method on the medium quality of fig. 1.a (3.a) and the very poor quality of fig. 1.b (3.b).
Minutiae extraction follows the fingerprint enhanced images. Figure 4 shows the minutiae from the medium quality fingerprint enhanced images of figures 2.a and 3.a (with the conventional and new methods respectively) by using the described marking algorithm. In the author’s approach, all the minutiae points (terminations and bifurcations) on the fingerprint image has been located and labeled. There is no false minutiae detection as compared to the result given by the classical method. In this ultimate result, not only there are some minutiae points that have not been labeled but there are also some points which are not considered as minutiae which have been labeled.
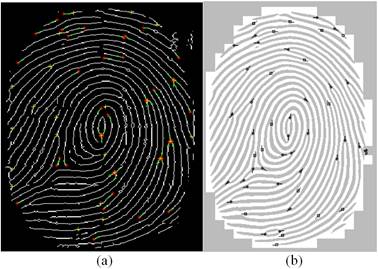
Figure 4. Minutiae extraction images from the medium quality original image of fig. 1.a with the classical method (4.a) and the proposed approach (4.b).
After successfully extracting the set of minutia points of fingerprint images, minutiae matching is performed to check whether they belong to the same person or not. This algorithm step is applied on the minutiae extraction images  of each person
of each person  (
( ) of the data base, based on each sample
) of the data base, based on each sample 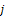 (
(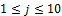 ) introduced by this different individual. So, for one fingerprint
) introduced by this different individual. So, for one fingerprint 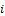 , we have a combination of 100 attempts. Then, we recorded the matching scores derived, the true acceptance rate (TAR) and the false rejection rate (FRR) vis-à-vis the threshold, for the two methods from all attempts.
, we have a combination of 100 attempts. Then, we recorded the matching scores derived, the true acceptance rate (TAR) and the false rejection rate (FRR) vis-à-vis the threshold, for the two methods from all attempts.
For a fingerprint test and its collected database, we observed that over the 100 tests performed and when fixing the threshold at 50%, a net appreciation of the recognition from the new method is observed. Still performing high, even at 80%, the system will recognize above the average, individuals in the database. And so, a mean of 20 fingerprint samples of TAR and FRR has been established. Looking at these two last threshold values considered and considering all the fingerprints, the mean reveals that the global matching performance is improved. And so, an assertion of a good performance in recognition of the algorithm can be established.
For the mismatching exercise, attempts are performed on one fingerprint image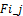 , to match with a different fingerprint in the same database. 200 tests related to the 20 individuals, have been carried out. We likewise produced the mean of the mismatching helping to have the global false acceptance rate (FAR) and the true rejection rate (TRR) of the methods. Considering the threshold values 20 to 40, the improved system presents a stagnant behavior meanwhile the classical one still fights to deny intruders. A good appreciation, on how strongly and decisively the new approach powerfully identifies intruders, is recorded from the new approach.
, to match with a different fingerprint in the same database. 200 tests related to the 20 individuals, have been carried out. We likewise produced the mean of the mismatching helping to have the global false acceptance rate (FAR) and the true rejection rate (TRR) of the methods. Considering the threshold values 20 to 40, the improved system presents a stagnant behavior meanwhile the classical one still fights to deny intruders. A good appreciation, on how strongly and decisively the new approach powerfully identifies intruders, is recorded from the new approach.
The matching and mismatching methods definitely helped, through the TAR and the TRR, to bring out the true success rate,. Issued from data performed, the curves presented in figures 5 and 6 portray the plotting of FAR, TRR and TSR for the conventional and improved methods respectively.

Figure 5. FAR, FRR and TSR functions for the classical method.
For the classical method, the FAR and FRR intersect at the equal error rate (EER) with coordinates (32.14%, 34.64%) in line with a precision of 65.36%. It displays a relative weakness in the appreciation of genuine and intruders.
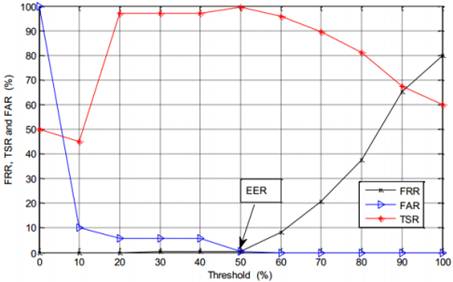
Figure 6. FAR, FRR and TSR functions for the new method.
For the author’s method, the FAR and FRR common point EER (50.11%, 0.73%) provides 99.27% in accuracy. A comparison between the two methods definitively shows the gap and presents an improvement of 33.91% in precision on behalf of the new method. The usability of the improved method will therefore be more relevant in consideration of the extent to which it will recognize, accept or reject with effectiveness, efficiency and satisfaction a genuine or an intruder.
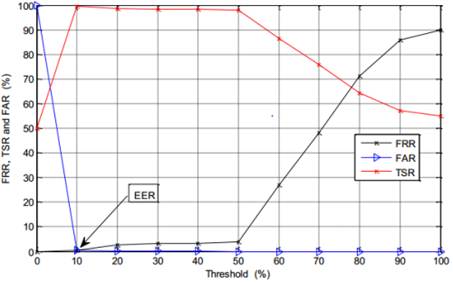
Figure 7. FAR, FRR and TSR functions by using the Gabor filtering and Sauvola’s thresholding techniques without the modified matching algorithm.
The implementation of Sangram’s technique on our database, and the finding of almost the same accuracy, discard the highest belief on the database influence in the final results and call henceforth to have a look at the steps used in the methodology. An analysis of the author’s algorithm performance highlights the impact of the ridge segmentation approach on one hand and the effect of the bounding box modification on the other hand. The running score between the two parts of this global system is implemented to put in the fore the added value of each sub-system. The corresponded plottings of FAR, FRR and TSR for the on-going point is drafted and presented in figure 7 with EER (10.02%, 1.02%). From this informed compliance, the Gabor filtering and Sauvola’s thresholding techniques have provided 98.98% in accuracy. That is an interest equivalent of 33.62% compared to the conventional approach. The tolerance parameters also lead the demand for 0.29% in precision on the global system. The improvement noticed from the conventional approach on the author’s method comes more from the Gabor filtering and Sauvola’s thresholding techniques at 99.14% than from the optimization of the tolerance parameters at 0.86%. The most innovation is from the first than from the second part of the approach. This sufficiency proves the limits of the mixture proposed by Sangram et al. [22]. Inter alia, we suspect the inadequate use of morphological functions for region of interest extraction in fingerprint image segmentation and ridge thinning which cannot be without adverse effects.
3.3. Discussion
The performance measures of algorithm in Biometrics verification are tools of understanding their intrinsic levels of giving faithful results. And so, evaluating biometric systems passes through the appreciation of the fundamentals of their implementation’ steps. The prevalence of 1.04% on the accuracy observed in comparing the author’s method with Yuliang He [35], denotes certainly in one hand, the verification of the hypothesis related to the nature of the database, and in the other hand the greater ability of the Gabor filtering and the Sauvola thresholding. The consideration of the variable bounding box in both the author’ system and Yuliang’s method reveals its performance in the matching exercise but also portrays how the focus on the minutiae recognition can be more powerful if the filtering technique is accurate.
The author’s algorithm still keeps ahead in precision with 7.27% for the hybrid matcher and 27.27% for the minutiae-based matcher when juxtaposed with Jain’s works [37]. Though the new method is using once the Gabor filtering and the minutiae-based matcher and Jain’s algorithm, It is exploiting a bank of 8 Gabor filters and a combination of matchers; the lead in accuracy is more pronounced in the new method for the minutiae-based comparison. This override may emanate from the change implemented in Jain’s filtering technique, the upgrading of the tolerance parameters values and/or the non-consideration of non-linear deformations present in the fingerprint.
Rajanna et al. [40] attempted a comparison study through which an approach based on the combination of Orientation Collinearity and Orientation Maps outclassed, with a difference in accuracy of 1.55%, the Gabor features. An understanding of this lead, before a technique using the Gabor’s procedure, certainly lies in the weakness of the steps combined with this last. The accuracy of the method developed in this paper shows the benefits of the proper use of Gabor’s filter.
The author’s implementation went further in outperforming the Multi Class Random Forest of Oblique Decision Trees of Thanh-Nghi Do et al. [42], though being so competitive with its occlusion and noise removal, its error reduction algorithm and its position ahead of six different techniques used during years.
Considering the previous, even powerful methods described in section I of image enhancement like Dual Tree Complex Wavelet Transform (DTCWT) introduced by Jossy [29], did not reach such a high-pitched value in precision. The combination of Gabor filters and Sauvola thresholding coupled with the minutiae-based matching methods and the research of the best triplet of tolerance parameters improved systematically the author’s approach compared to the nearly similar steps presented by Liu Wei-Chao [30] and Jain [37]. Moreover, all the traditional developments in fingerprint recognition based on implicit or explicit Euclidian distance comparison in minutiae [41, 40] or on the neural networks [32, 34, 43] did not permit to question a step in the author’s system. The analytical thinking over the methods from the literature and the new one helped to fling this last in better position for the high precision needed by a biometric system designed for such a pertinent issue: Public Insecurity.
4. Conclusion
We have recalled a conventional approach from [22] and presented a novel minutiae based fingerprint recognition method that achieve effective results. Admittedly, the two techniques followed the classical steps, especially fingerprint image enhancement and segmentation, minutiae extraction thinning and marking, false minutiae removal, minutiae alignment and matching. But, the new algorithm breaks fresh ground by performing the accuracy with only 0.73% of error rate when the conventional stays at 34.64%. This great stride forward comes with the use of the Gabor filtering than the Fast Fourier Transform for the fingerprint enhancement, the implementation of the Sauvola’s local thresholding than the local mean thresholding, the development of the elastic matching algorithm with optimized size of bounding box than the usual tolerance parameters.
The method has challenged almost the whole literature on the fingerprint recognition. It has even created hope to fight with the multi biometry systems like the combinational method for fusing the matching scores from fingerprint and voice subsystems under different noise levels [47] where the perfection is expressed at 100%, notwithstanding the fact that the process becomes severely expensive. With this level of efficiency, the results are quite similar to nearly perfect verification system and its mono biometric nature turns it to be more financially accessible. The method is therefore useful in favor of high insecurity context like terrorism over the world and especially in low-income countries.
References
- Joseph N. Pato and Lynette I. Millett. ‘‘Biometric Recognition: Challenges and Opportunities’’ Ed. Whither Biometrics Committee and National Research Council of the National Academies, Washington DC, USA, 2010.
- Mark Maguire ‘‘The Birth of Biometric Security’’ Anthropology Today, Vol. 25, Issue 2, April 2009.
- Emilio Mordini and Sonia Massari ‘‘Body, Biometrics and Identity’’ Bioethics, Vol. 22, Issue 9, pp. 488-498, 2008.
- Institute for Economics and Peace ‘‘Measuring and Understanding the Impact of Terrorism’’ Global Terrorism Index, Report 2015.
- Jodi M. Delgado ‘‘Use of Biometrics within Sub-Saharan Refugee Communities’’ IDA Document NS D-5082. H 13-001757, Mark Center Drive Alexandria, Virginia 2013.
- June Gibbs Brown ‘‘Birth Certificate Fraud’’ Department of health and Public Services, 0EI-07-99-00570, USA Sept. 2000.
- Magaret Gitai ‘‘Evidence of Identity and Citizenship: Papua’s New Guinea experiences and challenges’’ Iran ICAO Security and Facilitation TRIP Seminar, 9th – 11th May 2016.
- Christopher P. Raab ‘‘Fighting terrorism in an electronic age: does the patriot act unduly compromise our civil liberties?’’ Duke Law & Technology review, Vol. 2, 2006.
- A. K. Jain, Lin Hong, S. Pankanti and R. Bolle. ‘‘An identity-Authentication System using Fingerprints’’ Proceedings of the IEEE, Vol. 85, Issue 9, 1997.
- Benjamin Miller. ''Vital signs of identity.'' IEEE Spectrum. Vol. 31, Issue 2, pp: 22-30, 1994.
- Maltoni Davide, Dario Maio, Anil K. Jain, Salil Prabhakar. ''Handbook of fingerprint recognition'' 2nd edition, Springer-Verlag London Limited, New York, 2009.
- Penny Duquenoy, Carlisle George, Kai Kimppa, and Emilio Mordini ‘‘Ethical, Legal and Social Issues in Medical Informatics - Chapitre XI: Biometrics, Human Body, and Medicine: A Controversial History’’ IGI Global, Italy 2008.
- Daugman J., G. ''High Confidence Visual Recognition of Persons by a Test of Statistical Independence.'' IEEE Transactions on Pattern Analysis and Machine Intelligence. Vol. 15, issue 11, pp. 1148-1161. 1993.
- Clarke R. ''Human identification in information systems: Management challenges and public policy issues.'' Information Technology and People. Vol. 7, issue 4, pp. 6-37, 1994.
- Davies S., G. ''Touching big brother: How biometric technology will fuse flesh and machine.'' Information Technology and People. Vol. 7, issue 4, pp. 60-69, 1994.
- Newham E. ''The Biometric Report.'' SJB Services, New York, 1995.
- Drahanský Martin. ''Biometric Security Systems Fingerprint Recognition Technology'' Ph.D Thesis, BRNO University of Technology, Czech Republic, 2005.
- M. Gamassi, Massimo Lazzaroni, M. Misino, Vincenzo Piuri, D. Sana and F. Scotti. ‘‘Quality Assessment of Biometric Systems: A Comprehensive Perspective Based on Accuracy and Performance Measurement’’ IEEE Transactions on Instrumentation and Measurement. Vol. 54, pp 1489-1496, 2005.
- American National Standard for Information Systems ''Data Format for the Interchange of Fingerprint, Facial, & Scar Mark & Tattoo (SMT) Information.'' ANSI/NIST-ITL 1-2000, NIST Special Publication 500-245, 2000.
- Henry E., R. ''Classification and Uses of Finger Prints'' George Routledge and Sons ltd, London, 1900.
- Moenssens, A. A. ''Fingerprint Techniques'' Chilton Book Company, Philadelphia, 1971.
- Sangram Bana and Davinder Kaur ''Fingerprint Recognition using Image Segmentation'' International Journal Of Advanced Engineering Sciences And Technologies (IJAEST), Vol. 5, Issue 1, pp. 012 - 023, 2011.
- Richard O. Duda, Peter E. Hart and David G. Stork. ''Pattern Classification'' 2nd Edition, Wiley-Interscience, New York, USA, 2000.
- Francesco Turroni ''Fingerprint Recognition: Enhancement, Feature Extraction and Automatic Evaluation of Algorithms.'' Doctorate Thesis, University of Bologna, Italy, 2012.
- Bhawna Negi and Varun Sharma. ‘‘Fingerprint Recognition System’’ International Journal of Electronics and Computer Science Engineering (IJECSE), Vol. 1, Issue 3, pp 872-878, 2012.
- Roli Bansal, Priti Sehgal and Punam Bedi ‘‘Minutiae Extraction from Fingerprint Images - a Review’’ IJCSI International Journal of Computer Science Issues, Vol. 8, Issue 5, 2011.
- Alessandro Farina, Zsolt M. Kova´ cs-Vajna and Alberto Leone ''Fingerprint minutiae extraction from skeletonized binary images'' The Journal of Pattern Recognition Vol. 32, pp. 877—889, 1999.
- Shlomo Greenberg, Mayer Aladjem, Daniel Kogan and Itshak Dimitrov ''Fingerprint Image Enhancement Using Filtering Techniques'' IEEE, pp 322-325, 2000.
- Jossy P. George, Abhilash S. K. and Raja K. B. ‘‘Transform Domain Fingerprint Identification Based on DTCWT’’ International Journal of Advanced Computer Science and Applications (IJACSA), Vol. 3, Issue 1, 2012.
- Liu Wei-Chao and Guo Hong-Tao. ‘‘Occluded Fingerprint Recognition Algorithm Based on Multi Association Features Match’’ Journal of Multimedia, Vol. 9, Issue 7, July 2014.
- Ravi J., K. B. Raja and Venugopal K. R. ''Fingerprint recognition using minutia score matching'' International Journal of Engineering Science and Technology, Vol. 1, issue 2, pp: 35-42, 2009.
- Lokhande S. K., Dhongde V. S ''Fingerprint Identification System Based On Neural Network'' International Journal of Innovative Research in Science, Engineering and Technology (IJIRSET), Vol. 3, Special Issue 4, 2014.
- Prajakta M. M., Ramesh P. A. "A Novel Approach to Fingerprint Identification Using Gabor Filter-Bank" ACEEE International Journal on Network Security, Vol. 2, issue 3, 10-4, 2011.
- Hamsa, A. A. ''Fingerprint Identification System Using Neural Networks'' Nahrain University, College of Engineering Journal (NUCEJ), Vol. 15, pp. 234-244, 2012.
- Yuliang He, Jie Tian, Xiping Luo, Tanghui Zhang ‘‘Image enhancement and minutiae matching in fingerprint verification’’ Pattern Recognition Letters 24, 1349–1360, 2003.
- Shahadat Hossain, Rafiqul Islam "Fingerprint Matching Through Minutiae Based Feature Extraction Method" American Journal of Science and Technology, Vol. 2, No. 6, pp. 262-269, 2015.
- A. Jain, A. Ross and Salil Prabhakar. ‘‘Fingerprint Matching Using Minutiae and texture features’’ Proceedings of International Conference on Image Processing (ICIP), pp. 282-285, Thessaloniki, Greece, Oct 7-10, 2001.
- Anil K. Jain, Salil Prabhakar, Lin Hong, and Sharat Pankanti, "Filterbank-based fingerprint matching," IEEE Transactions on Image Processing, vol. 9, Issue 5, pp. 846–859, May 2000.
- A. Noor, N. Manivanan and W. Balachandran, "Transformation invariant algorithm for automatic fingerprint recognition" Electronics Letters, IET Journals & Magazines. Vol. 48, Issue 14, pp. 834-835, 2012.
- Rajanna, U., Erol, A., Bebis, G.: A comparative study on feature extraction for fingerprint classification and performance improvements using rank-level fusion. Patt. Anal. Appl. 13, 263–272, 2013.
- Paulino, A., Feng, J., Jain, A. K.: Latent fingerprint matching using descriptor-based Hough transform. IEEE Trans. Inform. Forensics Secur. 8 (1), 34, 2013.
- Thanh-Nghi Do, P. Lenca and S. Lallich "Classifying many-class high-dimensional fingerprint datasets using random forest of oblique decision trees" Vietnam Journal of Computer Science, Springer. Vol. 2, pp. 3–12, 2015.
- R. F. Nogueira, R. De A. Lotufo, R. C. Machado "Fingerprint Liveness Detection Using Convolutional Neural Networks" IEEE Transactions on Information Forensics and Security, IEEE Journals & Magazines. Volume: 11, Issue: 6, pp. 1206-1213, 2016.
- Hong Lin, Yifei Wan and Anil Jain. ''Fingerprint Image Enhancement: Algorithm and Performance Evaluation'' IEEE Transactions on Pattern Analysis and Machine Intelligence, Vol. 20, issue 8. pp. 777-789, 1998.
- J. Sauvola and M. Pietikainen ''Adaptive document image binarization.'' Pattern Recognition Vol. 33, issue 2, pp. 225–236, 2000.
- T. Y. Zhang and C. Y. Suen. ''A Fast Parallel Algorithm for Thinning Digital Patterns.'' Communications of the ACM, Vol. 27, issue 3. pp. 236-239, 1984.
- S. T. M. Anzar and P. S. Sathidevi. "On combining multi-normalization and ancillary measures for the optimal score level fusion of fingerprint and voice biometrics" EURASIP Journal on Advances in Signal Processing, Springer. Vol. 10, 2014.

 (Kanaa T. F. N.)
(Kanaa T. F. N.)  (Ele P.)
(Ele P.)  (Tchiotsop D.)
(Tchiotsop D.)  (Tonye E.)
(Tonye E.)